The Internet of Things (IoT) revolution continues to reshape industries by connecting devices and enabling smart data collection. As these networks grow, securing them becomes increasingly critical. IoT Core SSH AWS emerges as a powerful solution, leveraging Amazon Web Services (AWS) to provide a secure, scalable infrastructure for IoT applications. This integration ensures data integrity and confidentiality while facilitating seamless device management.
Securing IoT devices is paramount as they handle sensitive information and perform critical tasks. SSH (Secure Shell) serves as a robust protocol for secure communication, providing encrypted channels over unsecured networks. Integrating SSH with AWS IoT Core offers enhanced security features, allowing for safe device communication and management across the cloud. AWS's global presence and robust infrastructure further enhance the reliability and scalability of IoT solutions.
As organizations increasingly adopt IoT technologies, understanding the capabilities and benefits of IoT Core SSH AWS becomes essential. This article delves into the intricacies of this integration, exploring its advantages, architecture, and implementation strategies. Whether you're an enterprise looking to secure your IoT deployment or a developer seeking to enhance your IoT application's security, this comprehensive guide will provide valuable insights and practical advice.
Read also:Can Kissing Burn Calories The Unexpected Health Benefits
Table of Contents
- What is IoT Core SSH AWS?
- How Does IoT Core SSH Enhance Security?
- The Architecture of IoT Core SSH AWS
- Why Choose AWS for IoT Solutions?
- Implementing IoT Core SSH AWS in Your Infrastructure
- Best Practices for Using SSH in IoT
- Understanding AWS IoT Core Features
- How to Set Up Secure Connections with SSH?
- Challenges and Solutions in IoT Security
- Role of AWS in Enhancing IoT Security
- What Are the Benefits of Using IoT Core SSH AWS?
- Case Studies: IoT Core SSH AWS in Action
- Future Trends in IoT Security
- FAQs About IoT Core SSH AWS
- Conclusion
What is IoT Core SSH AWS?
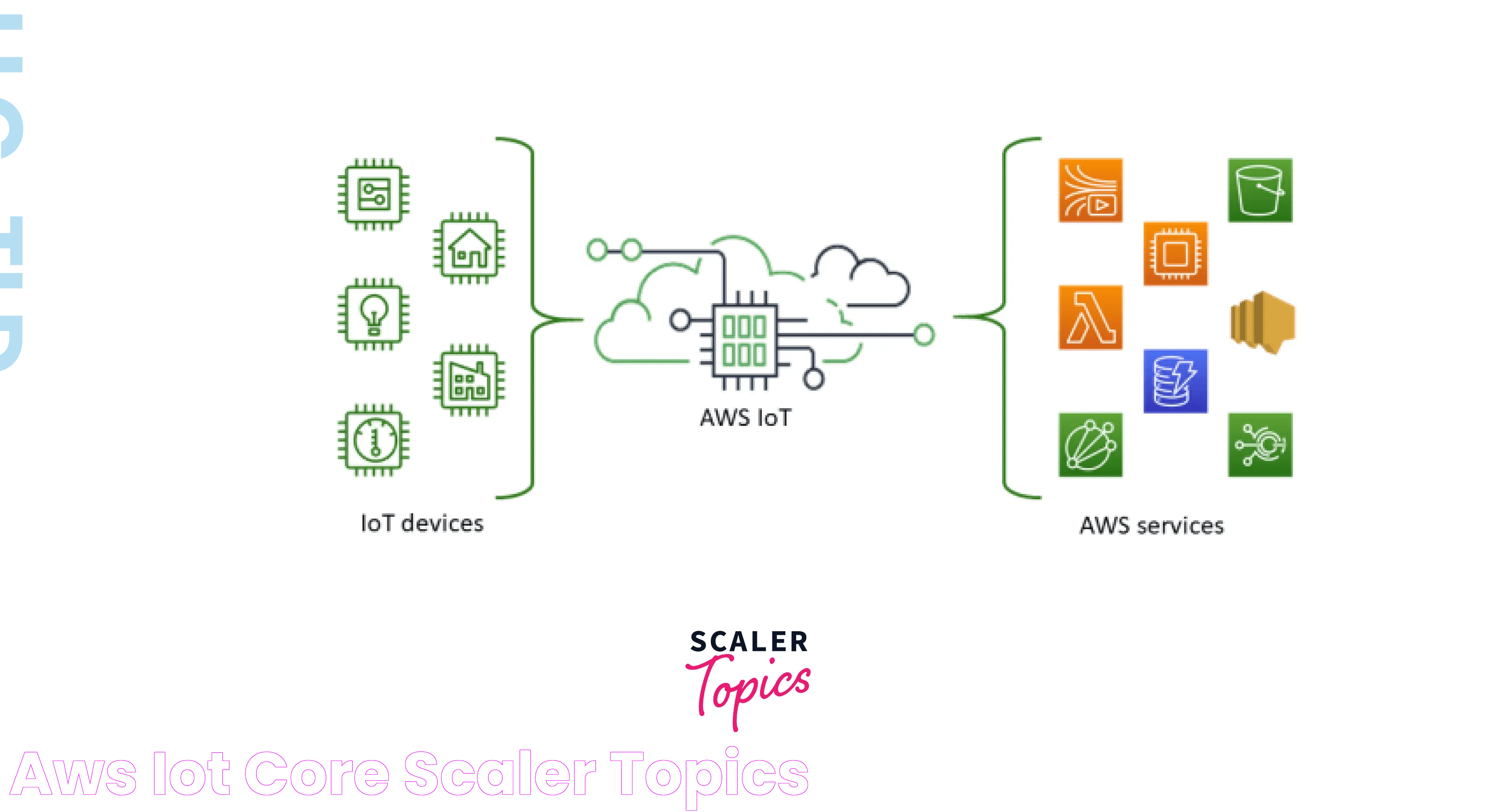
IoT Core SSH AWS is a comprehensive solution that merges IoT Core, a managed cloud service from Amazon, with SSH, a secure communication protocol. This integration offers a secure and scalable platform for IoT devices, providing encrypted channels for data transfer and remote management. By leveraging AWS's global infrastructure, IoT Core SSH AWS ensures high availability and reliability for IoT applications.
How Does IoT Core SSH Enhance Security?
IoT Core SSH enhances security by providing encrypted communication channels between IoT devices and cloud services. SSH's cryptographic protocols protect against eavesdropping and tampering, ensuring data integrity and confidentiality. This level of security is crucial for IoT networks, which often handle sensitive information and require robust protection against cyber threats.
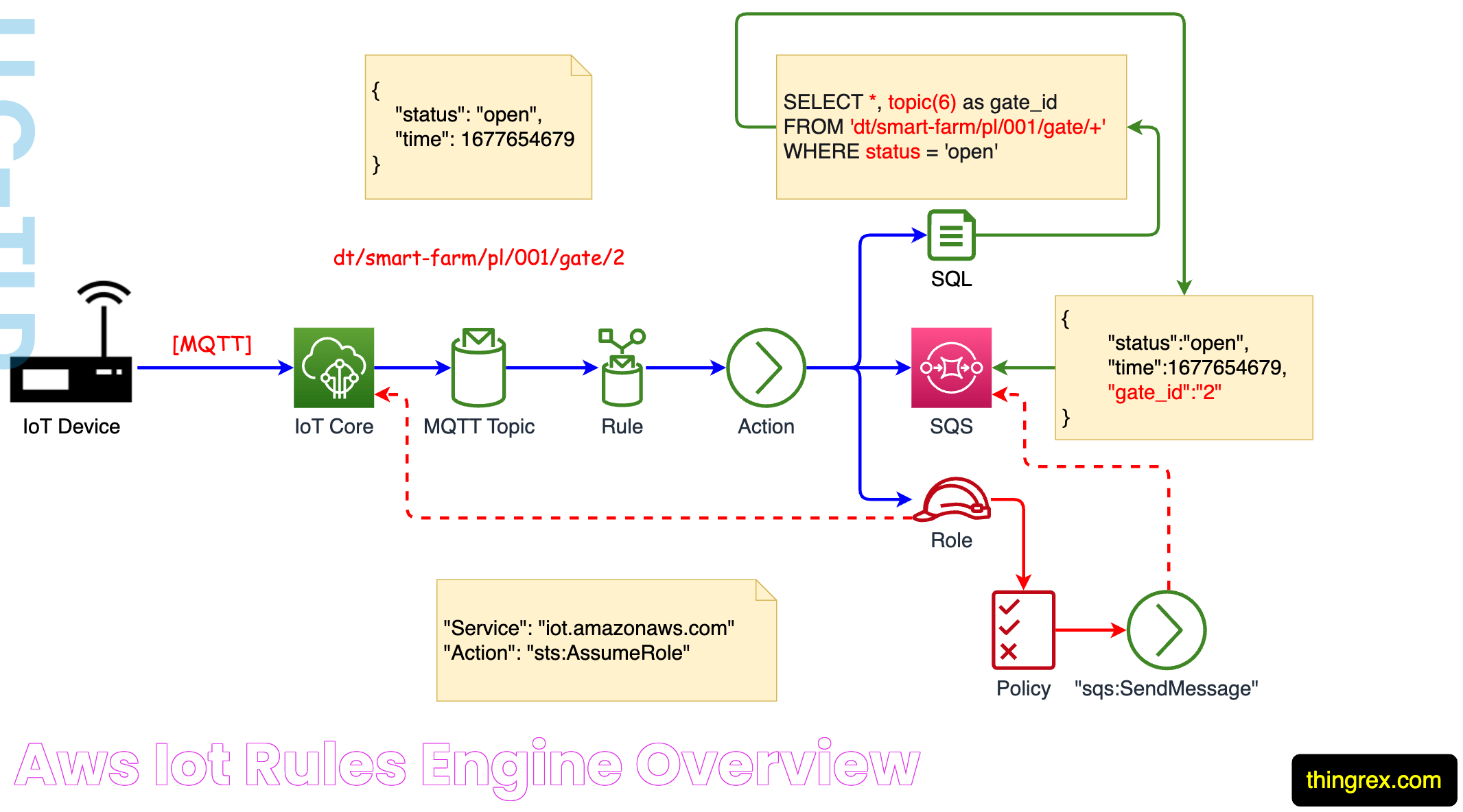
The Architecture of IoT Core SSH AWS
The architecture of IoT Core SSH AWS involves several components, including IoT devices, AWS IoT Core, and SSH protocols. IoT devices connect to AWS IoT Core over secure channels established by SSH. AWS IoT Core acts as a central hub, managing device connectivity and data flow. This architecture ensures secure and efficient communication between devices and cloud services.
Why Choose AWS for IoT Solutions?
AWS offers a wide range of services and features that make it an ideal choice for IoT solutions. Its global infrastructure provides high availability and scalability, while its security features ensure data protection and compliance with industry standards. AWS's robust ecosystem also supports various IoT protocols and integrations, making it a flexible and reliable platform for IoT deployments.
Implementing IoT Core SSH AWS in Your Infrastructure
Implementing IoT Core SSH AWS in your infrastructure involves several steps, including setting up AWS IoT Core, configuring SSH protocols, and connecting IoT devices. AWS provides comprehensive documentation and tools to facilitate this process, ensuring a seamless and efficient deployment. By following best practices and leveraging AWS's features, organizations can securely manage their IoT networks.
Best Practices for Using SSH in IoT
Using SSH in IoT requires adherence to several best practices to ensure optimal security and performance. These include:
Read also:Ryzen 7 2700 Power And Performance In One Package
- Regularly updating SSH keys and configurations to prevent unauthorized access.
- Using strong, unique passwords for SSH authentication.
- Implementing two-factor authentication for added security.
- Monitoring SSH activity for unusual patterns or unauthorized access attempts.
Understanding AWS IoT Core Features
AWS IoT Core offers a range of features that enhance IoT deployments. These include device management, data processing, and integration with other AWS services. AWS IoT Core also supports various IoT protocols, such as MQTT and HTTP, allowing for flexible and efficient communication between devices and cloud services.
How to Set Up Secure Connections with SSH?
Setting up secure connections with SSH involves several steps, including generating SSH keys, configuring SSH servers, and establishing encrypted channels. These steps ensure secure communication between IoT devices and cloud services, protecting against eavesdropping and tampering. AWS provides tools and documentation to facilitate this process, ensuring a seamless and efficient setup.
Challenges and Solutions in IoT Security
IoT security presents several challenges, including device vulnerabilities, data breaches, and unauthorized access. Addressing these challenges requires a comprehensive approach that includes robust encryption protocols, secure device management, and continuous monitoring. By leveraging AWS's security features and best practices, organizations can effectively mitigate these risks and protect their IoT networks.
Role of AWS in Enhancing IoT Security
AWS plays a crucial role in enhancing IoT security by providing a secure and scalable platform for IoT deployments. Its robust security features, including encryption protocols and compliance with industry standards, ensure data protection and integrity. AWS's global infrastructure also provides high availability and reliability, making it an ideal choice for secure IoT solutions.
What Are the Benefits of Using IoT Core SSH AWS?
Using IoT Core SSH AWS offers several benefits, including:
- Enhanced security through encrypted communication channels.
- Scalability and reliability offered by AWS's global infrastructure.
- Comprehensive tools and documentation for easy deployment and management.
- Integration with other AWS services for flexible and efficient IoT solutions.
Case Studies: IoT Core SSH AWS in Action
Several organizations have successfully implemented IoT Core SSH AWS in their infrastructure, achieving enhanced security and efficiency. These case studies highlight the benefits of this integration and provide valuable insights into its practical applications. Organizations across various industries have leveraged IoT Core SSH AWS to secure their IoT networks and improve their operations.
Future Trends in IoT Security
The future of IoT security is shaped by emerging technologies and evolving threats. As IoT networks continue to grow, so does the need for robust security measures. Future trends in IoT security include the adoption of advanced encryption protocols, integration with AI and machine learning, and the development of new standards and regulations. By staying ahead of these trends, organizations can ensure the security and reliability of their IoT deployments.
FAQs About IoT Core SSH AWS
1. What is the primary purpose of IoT Core SSH AWS?
The primary purpose of IoT Core SSH AWS is to provide a secure and scalable platform for IoT devices, enabling encrypted communication and efficient device management through AWS's robust infrastructure.
2. How does SSH improve IoT security?
SSH improves IoT security by providing encrypted communication channels, protecting data integrity and confidentiality, and preventing unauthorized access and tampering.
3. Can IoT Core SSH AWS be integrated with other AWS services?
Yes, IoT Core SSH AWS can be integrated with other AWS services, offering a flexible and comprehensive solution for IoT deployments and enabling efficient data processing and management.
4. What are the key features of AWS IoT Core?
AWS IoT Core offers features such as device management, data processing, support for various IoT protocols, and integration with other AWS services, enhancing the efficiency and scalability of IoT solutions.
5. How does AWS ensure the reliability of IoT Core SSH AWS?
AWS ensures the reliability of IoT Core SSH AWS through its global infrastructure, providing high availability and scalability for IoT deployments and ensuring seamless connectivity and data flow.
6. What are the common challenges in IoT security?
Common challenges in IoT security include device vulnerabilities, data breaches, unauthorized access, and evolving cyber threats, requiring comprehensive security measures and continuous monitoring to address effectively.
Conclusion
The integration of IoT Core SSH AWS offers a robust and scalable solution for securing IoT deployments. By leveraging AWS's infrastructure and SSH's encryption protocols, organizations can ensure the security and reliability of their IoT networks. As the IoT landscape continues to evolve, understanding and implementing IoT Core SSH AWS will be crucial for organizations seeking to enhance their IoT security and maximize the potential of their IoT applications.