The rapid growth of the Internet of Things (IoT) has transformed how we interact with our environment, enabling devices to communicate and perform tasks autonomously. A cornerstone of this technological evolution is the ability to manage these devices remotely, and one of the most efficient ways to achieve this is through the use of SSH keys on platforms like the Raspberry Pi. By employing SSH keys, users can secure their remote access to IoT devices, ensuring that data remains protected and operations run smoothly.
Raspberry Pi, a versatile single-board computer, has become a preferred choice for IoT enthusiasts due to its affordability, flexibility, and ease of use. When combined with an efficient remote IoT platform, it empowers users to connect, monitor, and control their devices from anywhere in the world. Implementing SSH keys in this setup enhances security by establishing encrypted connections that safeguard sensitive information from unauthorized access.
This article delves into the intricacies of using SSH keys with Raspberry Pi in remote IoT platforms, offering insights into the setup process, benefits, and best practices. Whether you're a beginner or a seasoned professional, understanding this integration will equip you with the knowledge to harness the full potential of your IoT devices securely and efficiently.
Read also:Can Kissing Burn Calories The Unexpected Health Benefits
Table of Contents
- What is IoT and Why is it Important?
- Understanding Raspberry Pi in IoT
- The Role of SSH Keys in Remote Access
- Setting Up SSH Key on Raspberry Pi
- How Do I Create an SSH Key?
- How Do I Secure My IoT Devices with SSH Keys?
- Remote IoT Platforms and Their Benefits
- Choosing the Right Remote IoT Platform
- Integrating SSH Keys with IoT Platforms
- How Does SSH Key Integration Enhance Security?
- Best Practices for Managing IoT Devices
- Troubleshooting Common SSH Key Issues
- Case Study: Successful IoT Projects Using SSH Keys
- What Are the Future Trends in IoT Security?
- FAQs
- Conclusion
What is IoT and Why is it Important?
The Internet of Things (IoT) refers to the network of physical objects embedded with sensors, software, and other technologies to connect and exchange data with other devices and systems over the internet. This connectivity allows for more direct integration of the physical world into computer-based systems, leading to improved efficiency, accuracy, and economic benefit.
IoT is important because it offers the ability to collect and analyze data remotely, enabling smarter and more informed decision-making. It has applications in various fields, including smart homes, healthcare, agriculture, and industrial automation, among others. The potential of IoT lies in its capacity to enhance productivity and innovation across numerous sectors.
Understanding Raspberry Pi in IoT
Raspberry Pi is a small, affordable, and versatile computer that has gained popularity in the IoT community due to its ability to handle a wide range of computing tasks. It can run multiple operating systems, including Linux, making it an ideal platform for developing IoT projects.
Its compact size and low power consumption make it suitable for deploying in various environments, from home automation to industrial applications. Raspberry Pi's GPIO (General Purpose Input/Output) pins allow it to interface with sensors and actuators, further extending its functionality in IoT projects.
The Role of SSH Keys in Remote Access
SSH (Secure Shell) keys are cryptographic keys used for securing connections between a client and a server. In the context of IoT, SSH keys provide a secure method for accessing and managing devices remotely, protecting data from potential breaches.
By using SSH keys, users can establish encrypted connections that prevent unauthorized access to their IoT devices. This is crucial for maintaining the integrity and confidentiality of the data being transmitted, especially in environments where sensitive information is involved.
Read also:Why Chickens Can Eat Bananas A Nutritional Insight
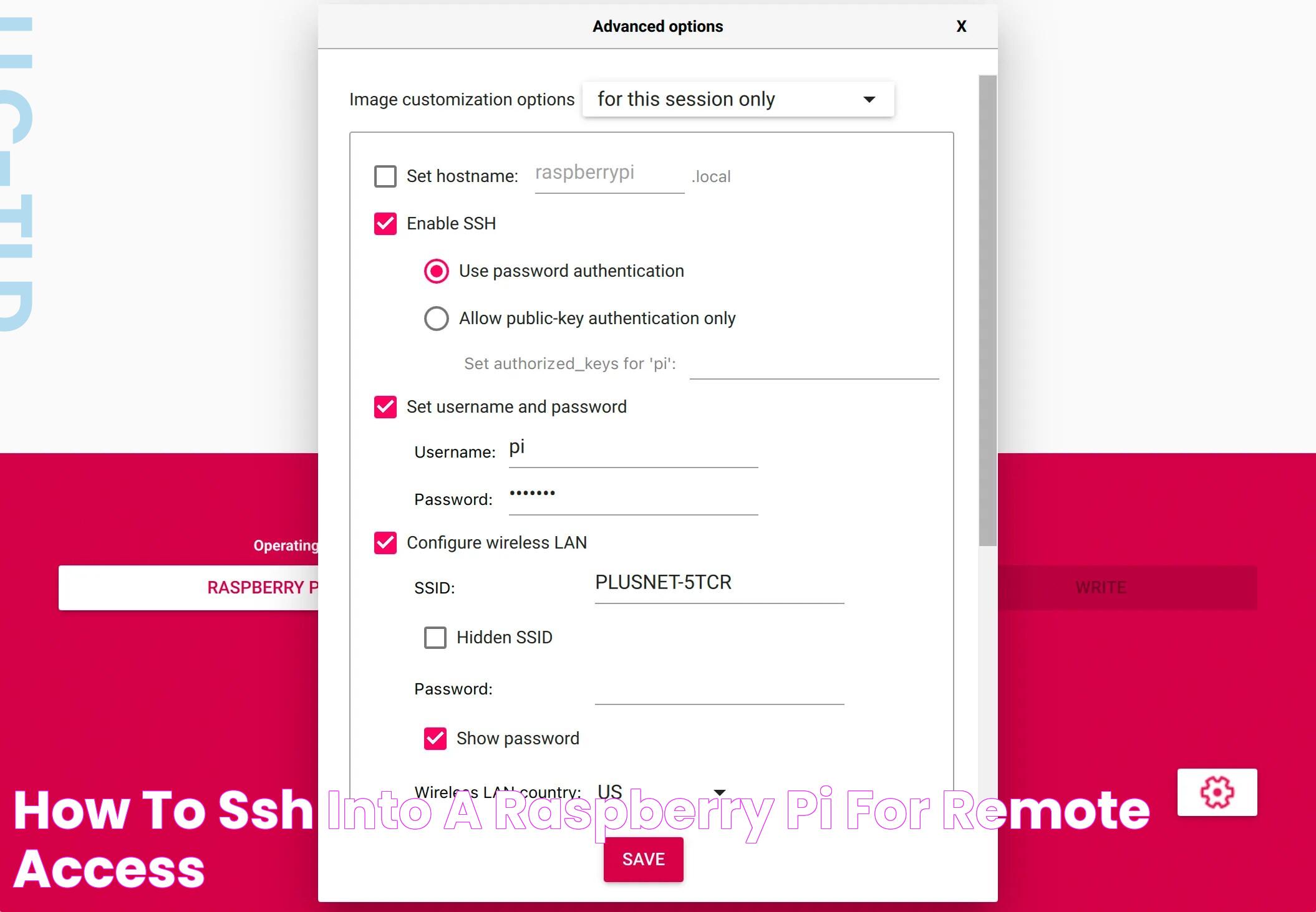
Setting Up SSH Key on Raspberry Pi
Setting up an SSH key on a Raspberry Pi involves generating a key pair on your client machine and uploading the public key to the Raspberry Pi. This process allows you to authenticate your connection without using a password, enhancing security and convenience.
- Generate an SSH key pair on your client machine using the terminal command:
ssh-keygen -t rsa -b 4096. - Copy the public key to the Raspberry Pi using the command:
ssh-copy-id user@raspberrypi. - Log in to the Raspberry Pi using the command:
ssh user@raspberrypiwithout a password.
This setup not only secures your connection but also streamlines the login process, making it easier to manage multiple devices.
How Do I Create an SSH Key?
Creating an SSH key is a straightforward process that involves generating a key pair on your client machine. Here's how you can do it:
- Open your terminal application.
- Run the command:
ssh-keygen -t rsa -b 4096. This will generate a 4096-bit RSA key pair, which is considered secure. - Follow the on-screen instructions to specify the file location and enter a passphrase if desired.
- Your SSH key pair will be saved in the specified directory, typically
~/.ssh.
Once generated, you can use the public key to authenticate connections with remote devices, eliminating the need for passwords.
How Do I Secure My IoT Devices with SSH Keys?
Securing IoT devices with SSH keys involves a few key steps to ensure that your data remains protected:
- Generate and Use SSH Keys: As mentioned earlier, generate SSH keys on your client machine and use the public key for authentication.
- Disable Password Authentication: Once SSH keys are set up, disable password authentication on your devices to prevent unauthorized access.
- Use Strong Passphrases: If you choose to use a passphrase with your SSH key, ensure it's strong and unique to add an extra layer of security.
- Regularly Update Systems: Keep your Raspberry Pi and other IoT devices updated with the latest security patches to protect against vulnerabilities.
By following these steps, you can significantly enhance the security of your IoT devices.
Remote IoT Platforms and Their Benefits
Remote IoT platforms play a crucial role in managing and controlling IoT devices from afar. These platforms provide a centralized interface for monitoring device status, collecting data, and executing commands, all while ensuring secure connectivity.
Some benefits of using remote IoT platforms include:
- Scalability: Easily manage a large number of devices from a single platform.
- Data Visualization: Analyze and visualize data collected from devices for better decision-making.
- Automation: Set up automated tasks and alerts for specific events, reducing manual intervention.
- Security: Implement robust security measures to protect data and devices from threats.
By leveraging remote IoT platforms, users can optimize their IoT operations and enhance productivity.
Choosing the Right Remote IoT Platform
Selecting the right remote IoT platform depends on various factors, including the scale of your project, the types of devices you're managing, and your specific requirements. When choosing a platform, consider the following aspects:
- Compatibility: Ensure the platform supports your devices and operating systems.
- Features: Look for features that align with your needs, such as data analytics, automation, and security.
- Ease of Use: Opt for a user-friendly interface that simplifies device management.
- Cost: Consider the pricing model and ensure it fits within your budget.
By evaluating these factors, you can choose a remote IoT platform that best suits your project objectives.
Integrating SSH Keys with IoT Platforms
Integrating SSH keys with IoT platforms enhances security by providing encrypted communication between devices and the platform. This integration ensures that sensitive data remains confidential and protected from unauthorized access.
To integrate SSH keys with your IoT platform:
- Generate SSH Keys: Follow the steps mentioned earlier to generate SSH keys on your client machine.
- Configure the Platform: Upload the public key to the IoT platform's settings to enable key-based authentication.
- Test the Connection: Verify that you can access your devices securely using the SSH keys.
By setting up this integration, you can ensure that your IoT operations are both secure and efficient.
How Does SSH Key Integration Enhance Security?
SSH key integration enhances security by providing a robust authentication mechanism that eliminates the vulnerabilities associated with password-based access. Here's how it works:
- Encryption: SSH keys use encryption to protect data during transmission, ensuring that it cannot be intercepted or tampered with.
- Eliminates Passwords: By replacing passwords with SSH keys, you reduce the risk of brute-force attacks and unauthorized access.
- Access Control: SSH keys allow for precise access control, ensuring that only authorized users can access devices.
Overall, SSH key integration provides a secure and reliable method for managing IoT devices remotely.
Best Practices for Managing IoT Devices
Effective management of IoT devices involves implementing best practices to ensure security, efficiency, and reliability. Here are some key practices to consider:
- Regular Updates: Keep devices up to date with the latest firmware and security patches to protect against vulnerabilities.
- Strong Authentication: Use strong authentication methods, such as SSH keys, to secure access to devices.
- Monitor Activity: Continuously monitor device activity for any unusual behavior that may indicate a security breach.
- Data Encryption: Encrypt data both at rest and in transit to protect sensitive information.
- Backup and Recovery: Implement robust backup and recovery plans to ensure data integrity in case of failure.
By following these practices, you can effectively manage your IoT devices and mitigate potential risks.
Troubleshooting Common SSH Key Issues
While SSH keys are a reliable method for securing connections, users may encounter common issues during setup and usage. Here are some troubleshooting tips:
- Permission Denied: Ensure that the correct permissions are set for the
~/.sshdirectory and files. The directory should have700permissions, and the private key file should have600permissions. - Key Not Recognized: Verify that the public key is correctly added to the
authorized_keysfile on the remote device. - Connection Timeout: Check the network connection and ensure that the remote device is accessible.
- Passphrase Issues: If using a passphrase, ensure that it's entered correctly when prompted.
By addressing these issues, you can ensure a smooth and secure experience with SSH keys.
Case Study: Successful IoT Projects Using SSH Keys
Many successful IoT projects have leveraged SSH keys to enhance security and efficiency. One notable example is a smart city initiative where Raspberry Pi devices were used to monitor and control street lighting.
In this project:
- SSH keys were used to establish secure connections between the central control system and individual light controllers.
- Remote IoT platforms enabled real-time monitoring and data collection, optimizing energy usage and reducing costs.
- The use of SSH keys prevented unauthorized access, ensuring that only authorized personnel could modify settings or access data.
This case study highlights the benefits of using SSH keys in IoT projects, demonstrating their ability to enhance security and operational efficiency.
What Are the Future Trends in IoT Security?
The landscape of IoT security is constantly evolving, with new trends emerging to address the increasing challenges. Some future trends in IoT security include:
- AI and Machine Learning: Leveraging artificial intelligence and machine learning to detect and respond to security threats in real-time.
- Blockchain Technology: Using blockchain for secure and transparent data transactions, enhancing trust and accountability.
- Edge Computing: Implementing security measures at the edge of the network to reduce latency and improve data privacy.
- Zero Trust Architecture: Adopting a zero-trust approach to ensure that every access request is authenticated and authorized, regardless of the source.
These trends indicate a shift towards more sophisticated and comprehensive security strategies in the IoT domain.
FAQs
1. How do I know if my SSH key is secure?
Ensure your SSH key is secure by using a strong passphrase, keeping it in a secure location, and regularly updating your systems.
2. Can I use SSH keys for multiple IoT devices?
Yes, you can use the same SSH key pair for multiple devices, but it's recommended to use separate keys for better security management.
3. What should I do if I lose my SSH private key?
If you lose your SSH private key, generate a new key pair and update the public key on all devices to maintain access.
4. Are there alternatives to SSH keys for securing IoT devices?
Alternative methods include VPNs and two-factor authentication, but SSH keys are preferred for their simplicity and security.
5. How often should I change my SSH keys?
Regularly rotate your SSH keys, especially if you suspect they've been compromised or if personnel changes occur.
6. Can SSH keys be used on platforms other than Raspberry Pi?
Yes, SSH keys can be used on various platforms, including Linux servers and cloud-based environments, for secure access.
Conclusion
The integration of SSH keys with Raspberry Pi in remote IoT platforms represents a significant advancement in securing and managing IoT devices. By understanding the underlying principles and best practices, users can enhance the security and efficiency of their IoT operations. As technology continues to evolve, embracing these security measures will be essential for protecting sensitive data and ensuring the success of future IoT projects.