In the world of the Internet of Things (IoT), seamless and efficient remote access is a critical component of building a successful network of devices. One of the most popular methods for accessing and managing IoT devices remotely is through Secure Shell (SSH) on a Raspberry Pi. However, the traditional setup of SSH can be cumbersome and time-consuming, especially for beginners and those who seek a more straightforward approach. This article delves into the innovative methods of establishing remote access on IoT platforms by downloading SSH on Raspberry Pi without the usual complexities.
As IoT continues to revolutionize various industries, the demand for efficient remote management tools has grown exponentially. Raspberry Pi, a popular choice for IoT developers and hobbyists alike, offers a compact and cost-effective solution. However, setting up SSH traditionally involves several configuration steps that could be daunting for those unfamiliar with network protocols. This article aims to simplify the process by exploring alternative methods that eliminate the need for intricate configurations, enabling users to focus on their IoT projects.
By leveraging these innovative techniques, users can streamline their remote access setup, enhancing the efficiency of their IoT systems. Whether you're a seasoned developer or a newcomer to the IoT landscape, understanding how to effectively manage Raspberry Pi devices remotely is essential. This guide will provide you with the knowledge and tools needed to implement SSH on your Raspberry Pi effortlessly, without the usual setup challenges. Read on to discover how you can enhance your IoT projects with seamless remote access solutions.
Read also:Pizza Hut A Delicious Overview Beyond Social Media Platforms
Table of Contents
- What is IoT and Why is it Important?
- Understanding SSH and Its Benefits
- Why Choose Raspberry Pi for IoT Projects?
- How to Setup SSH on Raspberry Pi?
- Advantages of Remote Access via SSH
- Common Challenges in SSH Setup and How to Overcome Them?
- Role of IoT Platforms in Enhancing Remote Access
- Security Considerations for IoT SSH Access
- Exploring Alternative Remote Access Methods
- How to Optimize Raspberry Pi Performance for IoT?
- Case Studies: Success Stories of IoT SSH Implementation
- Future Trends in Remote Access and IoT
- FAQs
- Conclusion
What is IoT and Why is it Important?
The Internet of Things, commonly referred to as IoT, is a network of interconnected devices that communicate and exchange data with each other. These devices, ranging from household appliances to industrial machinery, are embedded with sensors, software, and other technologies that enable them to connect to the internet and share information. IoT is important because it allows for enhanced data collection, analysis, and automation, which leads to improved efficiency, productivity, and decision-making across various sectors.
One of the key benefits of IoT is its ability to provide real-time insights and analytics. By collecting data from connected devices, businesses can gain valuable insights into their operations, customer behavior, and market trends. This data-driven approach allows for better decision-making and strategic planning. Additionally, IoT enables automation of processes, reducing the need for manual intervention and minimizing errors. This not only saves time and resources but also enhances the overall efficiency of operations.
Moreover, IoT has the potential to revolutionize industries by creating new business models and revenue streams. For instance, IoT-enabled smart homes allow homeowners to control their appliances and devices remotely, leading to increased convenience and energy efficiency. In the healthcare sector, IoT devices can monitor patients' vital signs and provide real-time updates to healthcare providers, improving patient care and outcomes. The possibilities of IoT are endless, and its impact on various sectors is expected to grow significantly in the coming years.
Understanding SSH and Its Benefits
Secure Shell, or SSH, is a cryptographic network protocol used for secure communication between devices over an unsecured network. SSH provides a secure channel through which users can access and manage devices remotely, ensuring that data transmitted between the devices remains confidential and protected from unauthorized access. This is particularly important in the context of IoT, where devices are often distributed across various locations and connected to potentially vulnerable networks.
One of the primary benefits of SSH is its ability to provide secure remote access to devices. By using SSH, users can manage and configure their devices from anywhere in the world, without having to be physically present. This is especially useful for IoT deployments, where devices may be located in remote or hard-to-reach areas. SSH also allows for secure file transfers between devices, enabling users to easily exchange data and perform updates or backups.
Another advantage of SSH is its support for strong authentication methods, such as public key authentication. This ensures that only authorized users can access the devices, reducing the risk of unauthorized access and potential security breaches. Furthermore, SSH provides encryption of data transmitted between devices, ensuring that sensitive information remains confidential and protected from eavesdropping or tampering. Overall, SSH is a powerful tool for enhancing the security and efficiency of remote device management in IoT environments.
Read also:Polar Vs Non Polar A Comprehensive Guide To Understanding Their Differences
Why Choose Raspberry Pi for IoT Projects?
Raspberry Pi is a popular choice for IoT projects due to its affordability, versatility, and ease of use. As a small, single-board computer, Raspberry Pi offers a cost-effective solution for developing and deploying IoT devices. Its low price point makes it accessible to hobbyists, students, and professionals alike, allowing for experimentation and innovation without breaking the bank.
One of the key advantages of Raspberry Pi is its versatility. It is compatible with a wide range of operating systems, including Linux-based distributions such as Raspbian, Ubuntu, and Debian. This flexibility allows users to choose the operating system that best suits their needs and preferences. Additionally, Raspberry Pi supports a variety of programming languages, including Python, Java, and C++, making it an ideal platform for developers with different skill sets and expertise.
Raspberry Pi also offers extensive connectivity options, including Ethernet, Wi-Fi, and Bluetooth, enabling seamless integration with other devices and networks. This makes it an excellent choice for IoT projects that require reliable and stable communication between devices. Furthermore, Raspberry Pi's GPIO pins allow for easy connection to sensors, actuators, and other peripherals, facilitating the development of custom IoT solutions tailored to specific use cases.
Overall, Raspberry Pi's affordability, versatility, and connectivity options make it a popular choice for IoT projects. Whether you're a beginner looking to explore the world of IoT or an experienced developer seeking a cost-effective platform for prototyping and deployment, Raspberry Pi offers a reliable and flexible solution that meets a wide range of needs and requirements.
How to Setup SSH on Raspberry Pi?
Traditional Methods of Setting Up SSH
Setting up SSH on Raspberry Pi traditionally involves several steps, including installing the necessary software, configuring the network settings, and enabling the SSH service. These steps can be time-consuming and challenging for beginners, especially those unfamiliar with command-line interfaces and network protocols.
The first step in setting up SSH on Raspberry Pi is to install the necessary software. This typically involves installing the OpenSSH package, which provides the SSH client and server components. Once the software is installed, users need to configure the network settings to ensure that the Raspberry Pi can communicate with other devices on the network. This may involve setting a static IP address or configuring DHCP settings, depending on the network environment.
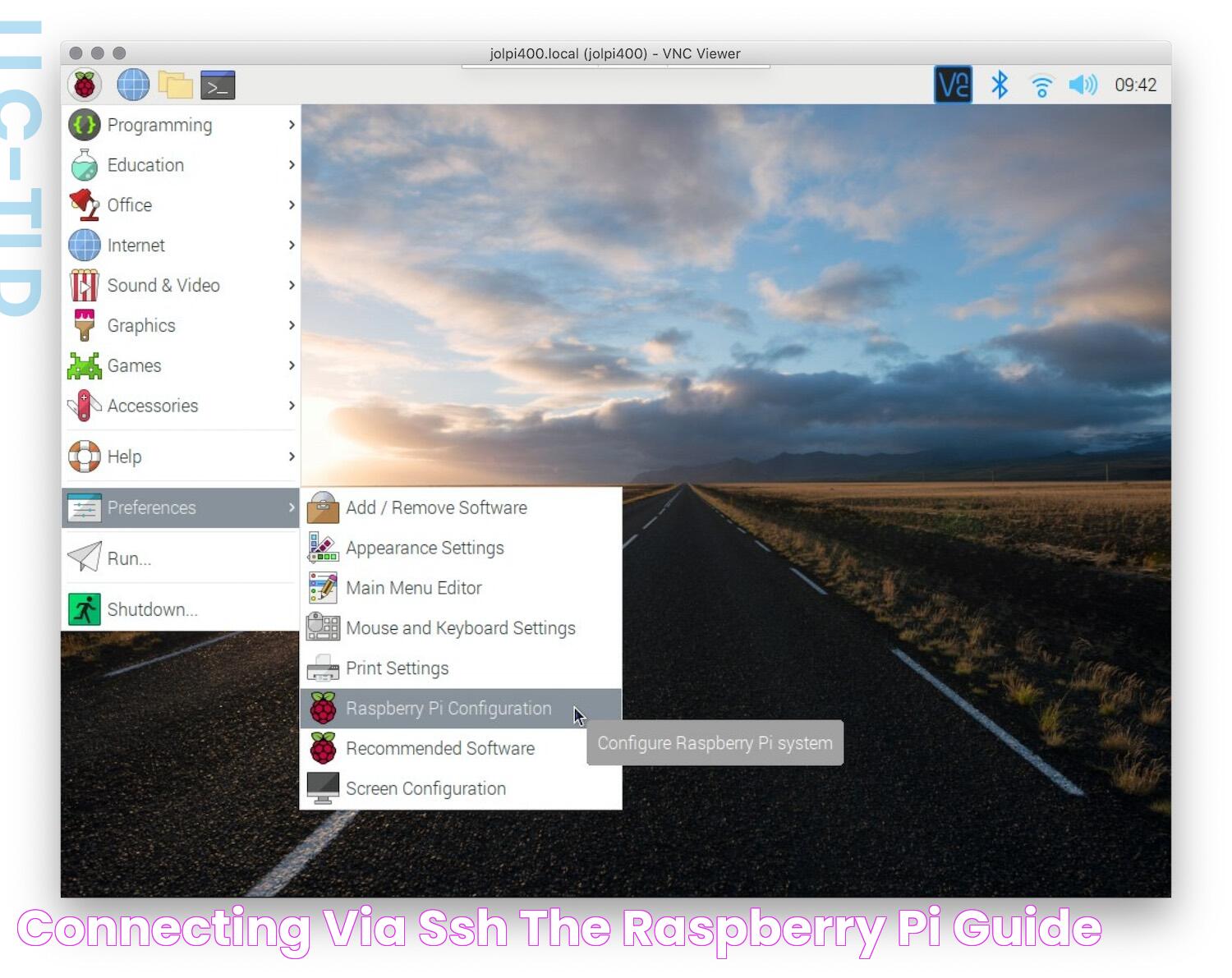
After the network settings are configured, users need to enable the SSH service on the Raspberry Pi. This can be done by accessing the Raspberry Pi configuration tool and selecting the option to enable SSH. Once the service is enabled, users can connect to the Raspberry Pi remotely using an SSH client, such as PuTTY or OpenSSH, by entering the device's IP address and authentication credentials.
While the traditional method of setting up SSH on Raspberry Pi provides a secure and reliable solution, it can be challenging for beginners and those seeking a more streamlined approach. Fortunately, there are alternative methods available that simplify the process and eliminate the need for complex configurations, making it easier for users to access and manage their Raspberry Pi devices remotely.
Innovative Methods to Download SSH Without Hassles
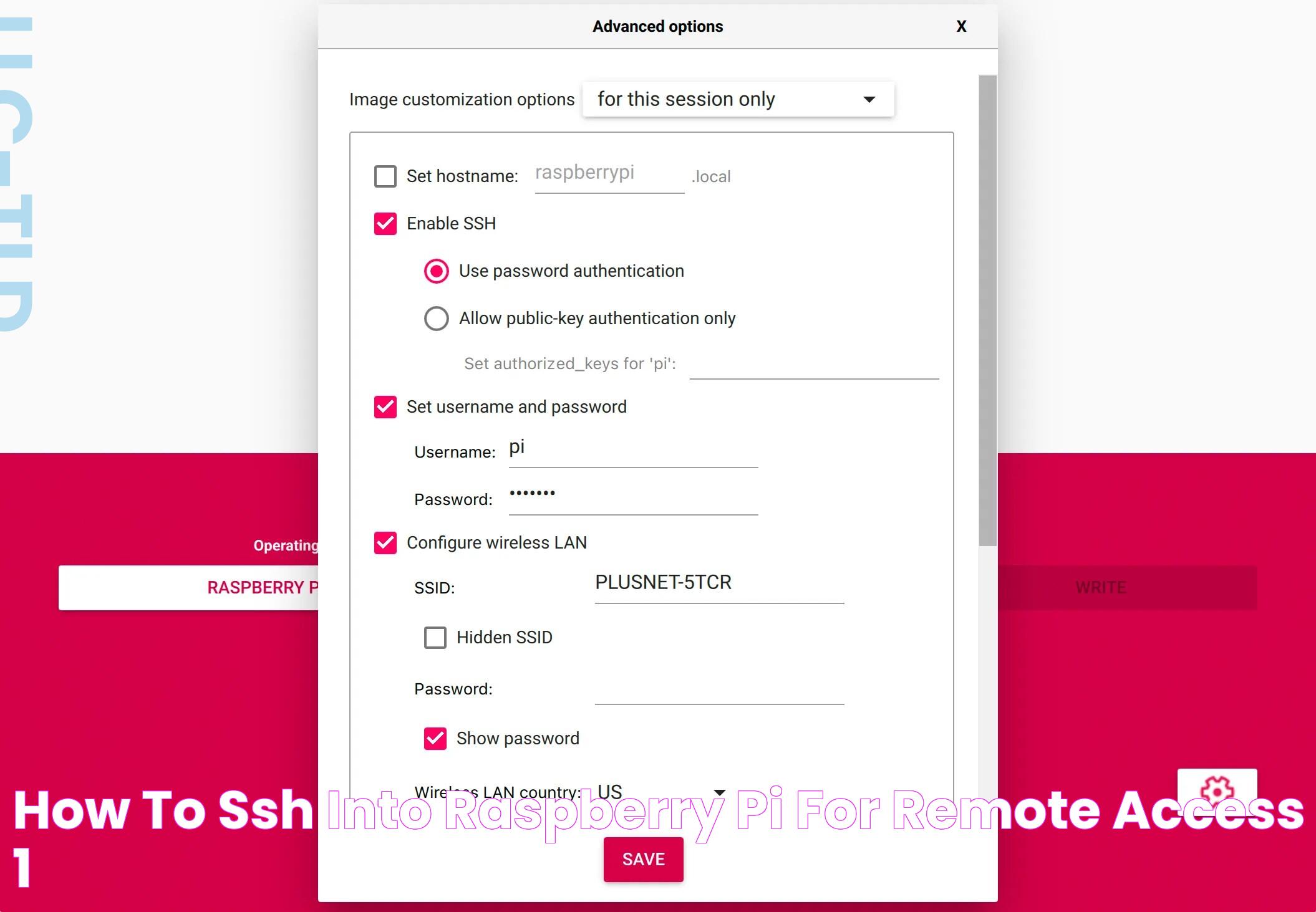
To simplify the process of setting up SSH on Raspberry Pi, several innovative methods have emerged that eliminate the need for complex configurations. One such method involves using pre-configured images that come with SSH enabled by default. These images can be downloaded and installed on the Raspberry Pi, allowing users to access the device remotely without having to manually configure the network settings or enable the SSH service.
Another approach involves using cloud-based IoT platforms that provide built-in SSH access. These platforms offer a user-friendly interface that allows users to manage their Raspberry Pi devices remotely without having to configure SSH manually. By leveraging these platforms, users can focus on their IoT projects and development tasks, rather than spending time on network configurations and SSH setup.
Additionally, some tools and scripts are available that automate the process of setting up SSH on Raspberry Pi. These tools simplify the process by providing a guided setup experience, allowing users to configure SSH with just a few clicks. This approach is particularly useful for beginners and those seeking a more streamlined solution for remote access.
By adopting these innovative methods, users can set up SSH on Raspberry Pi without the usual hassles, enhancing the efficiency and productivity of their IoT projects. Whether you're a beginner or an experienced developer, these methods provide a convenient and reliable solution for accessing and managing Raspberry Pi devices remotely.
Advantages of Remote Access via SSH
Remote access via SSH offers numerous advantages for managing IoT devices, particularly when using platforms like Raspberry Pi. One of the primary benefits is the ability to manage devices from anywhere in the world, without the need for physical presence. This is especially useful for IoT deployments where devices are distributed across various locations or situated in remote areas.
SSH provides a secure and encrypted channel for communication, ensuring that data transmitted between devices remains confidential and protected from unauthorized access. This is crucial for maintaining the security and integrity of IoT networks, where sensitive data is often exchanged. By using SSH, users can perform administrative tasks, configure settings, and troubleshoot issues without compromising the security of their devices.
Another advantage of remote access via SSH is the flexibility it offers in terms of device management. Users can easily transfer files between devices, execute commands, and run scripts remotely, streamlining the process of managing and updating IoT devices. This reduces the need for manual intervention and allows for more efficient maintenance and monitoring of IoT networks.
Moreover, SSH enables seamless integration with other tools and platforms, allowing for enhanced automation and orchestration of IoT systems. By leveraging SSH, users can automate routine tasks, schedule updates, and implement custom workflows, improving the overall efficiency and productivity of their IoT projects.
Overall, remote access via SSH provides a secure, flexible, and efficient solution for managing IoT devices, enhancing the capabilities and performance of IoT networks and enabling users to focus on their core development and innovation tasks.
Common Challenges in SSH Setup and How to Overcome Them?
Setting up SSH on IoT devices like Raspberry Pi can present several challenges, particularly for beginners and those unfamiliar with network protocols. One common challenge is configuring network settings, such as setting a static IP address or configuring DHCP. This can be complex and time-consuming, especially in environments with multiple devices and network configurations.
Another challenge is ensuring that the SSH service is enabled and properly configured on the device. Beginners may struggle with accessing the Raspberry Pi configuration tool or using command-line interfaces to enable and configure the SSH service. Additionally, troubleshooting connectivity issues and resolving network-related errors can be daunting for those new to IoT and network management.
To overcome these challenges, users can leverage pre-configured images that come with SSH enabled by default. These images simplify the setup process by eliminating the need for manual network configuration and service enabling, allowing users to focus on their IoT projects. Additionally, cloud-based IoT platforms offer built-in SSH access, providing a user-friendly interface for managing devices remotely without the need for complex configurations.
Furthermore, several tools and scripts are available that automate the process of setting up SSH on Raspberry Pi. These tools provide guided setup experiences, simplifying the configuration process and reducing the likelihood of errors. By leveraging these resources, users can overcome common challenges in SSH setup and ensure a smooth and efficient remote access experience.
Role of IoT Platforms in Enhancing Remote Access
IoT platforms play a crucial role in enhancing remote access to devices by providing a centralized and user-friendly interface for managing and monitoring IoT networks. These platforms offer a range of tools and features that simplify the process of setting up and configuring remote access, allowing users to focus on their core development and innovation tasks.
One of the key advantages of IoT platforms is their ability to provide built-in SSH access, eliminating the need for manual configuration and setup. This simplifies the process of managing and accessing devices remotely, reducing the time and effort required for network configuration and troubleshooting. By using an IoT platform, users can easily connect to their devices and perform administrative tasks, configure settings, and troubleshoot issues without having to navigate complex network protocols.
IoT platforms also offer enhanced security features, such as encryption and authentication, ensuring that data transmitted between devices remains confidential and protected from unauthorized access. This is crucial for maintaining the security and integrity of IoT networks, where sensitive data is often exchanged. Additionally, IoT platforms provide seamless integration with other tools and services, allowing for enhanced automation and orchestration of IoT systems.
Overall, IoT platforms play a vital role in enhancing remote access by providing a centralized and user-friendly interface for managing IoT devices. By leveraging these platforms, users can streamline the process of setting up and configuring remote access, improving the efficiency and productivity of their IoT projects and enabling them to focus on their core development and innovation tasks.
Security Considerations for IoT SSH Access
Security is a critical consideration when setting up SSH access for IoT devices, as these devices are often distributed across various locations and connected to potentially vulnerable networks. To ensure the security and integrity of IoT networks, it's important to implement robust security measures and best practices when configuring SSH access.
One of the primary security considerations for IoT SSH access is the use of strong authentication methods, such as public key authentication. This ensures that only authorized users can access the devices, reducing the risk of unauthorized access and potential security breaches. Additionally, it's important to use complex passwords and regularly update them to prevent unauthorized access to the devices.
Another important security consideration is the encryption of data transmitted between devices. SSH provides a secure and encrypted channel for communication, ensuring that data remains confidential and protected from eavesdropping or tampering. It's important to use strong encryption algorithms and regularly update them to ensure the continued security of data transmission.
Additionally, it's important to regularly monitor and audit SSH access logs to detect any suspicious activity or unauthorized access attempts. This allows for timely identification and mitigation of potential security threats, ensuring the continued security and integrity of IoT networks. Overall, by implementing robust security measures and best practices, users can ensure the security and integrity of their IoT networks and maintain the confidentiality and protection of sensitive data.
Exploring Alternative Remote Access Methods
While SSH is a popular method for remote access to IoT devices, there are alternative methods available that offer different features and capabilities. These methods provide users with a range of options for managing and accessing their IoT devices, depending on their specific needs and requirements.
One alternative method for remote access is the use of Virtual Network Computing (VNC), which allows users to access and control devices remotely through a graphical user interface. VNC provides a more user-friendly experience compared to command-line interfaces, making it an ideal choice for beginners and those who prefer a visual approach to device management. Additionally, VNC supports cross-platform access, allowing users to connect to their devices from a variety of devices and operating systems.
Another alternative method is the use of cloud-based IoT platforms that offer built-in remote access capabilities. These platforms provide a centralized and user-friendly interface for managing and monitoring IoT devices, eliminating the need for manual configuration and setup. By leveraging these platforms, users can easily connect to their devices and perform administrative tasks, configure settings, and troubleshoot issues without having to navigate complex network protocols.
Furthermore, the use of remote desktop protocols, such as Remote Desktop Protocol (RDP) and Secure Shell File Transfer Protocol (SFTP), provides additional options for remote access. These protocols offer secure and encrypted channels for communication, ensuring that data transmitted between devices remains confidential and protected from unauthorized access.
Overall, by exploring alternative remote access methods, users can choose the solution that best fits their needs and preferences, enhancing the efficiency and productivity of their IoT projects and enabling them to focus on their core development and innovation tasks.
How to Optimize Raspberry Pi Performance for IoT?
Optimizing Raspberry Pi performance is crucial for ensuring the efficiency and reliability of IoT projects. By implementing various optimization techniques and best practices, users can enhance the performance of their Raspberry Pi devices and ensure the smooth operation of their IoT networks.
One of the key factors in optimizing Raspberry Pi performance is selecting the right operating system and software. It's important to choose an operating system that is lightweight and optimized for IoT applications, such as Raspbian or Ubuntu. Additionally, users should regularly update their software and operating systems to ensure they are running the latest versions and patches, reducing the risk of security vulnerabilities and performance issues.
Another important consideration is resource management. Raspberry Pi devices have limited resources, so it's essential to monitor and manage CPU, memory, and storage usage to prevent performance bottlenecks. Users can use tools like htop and iotop to monitor resource usage and identify any potential issues. Additionally, optimizing the code and scripts running on the Raspberry Pi can help reduce resource usage and improve performance.
Furthermore, optimizing network settings can enhance Raspberry Pi performance. Ensuring a stable and reliable network connection is crucial for IoT applications, as connectivity issues can lead to delays and interruptions. Users can optimize network settings by configuring a static IP address, enabling Quality of Service (QoS) settings, and using a reliable DNS server.
Overall, by implementing these optimization techniques and best practices, users can enhance the performance of their Raspberry Pi devices and ensure the smooth operation of their IoT projects, improving efficiency and reliability.
Case Studies: Success Stories of IoT SSH Implementation
There are numerous success stories of IoT SSH implementation, showcasing the benefits and capabilities of this powerful remote access method. These case studies highlight how organizations and individuals have leveraged SSH to enhance the efficiency and productivity of their IoT projects and achieve their goals.
One notable case study is the implementation of IoT SSH in a smart agriculture project. By using SSH, the project team was able to remotely manage and monitor their network of IoT devices, including sensors and actuators, distributed across various farm locations. This allowed them to collect real-time data on soil moisture, temperature, and other environmental factors, enabling them to make data-driven decisions and optimize their agricultural operations.
Another success story involves the use of IoT SSH in a smart city initiative. In this project, the city leveraged SSH to remotely manage a network of IoT devices, including smart lighting, traffic sensors, and environmental monitoring systems. By using SSH, the city was able to efficiently monitor and control these devices, improving the overall efficiency and sustainability of their urban infrastructure.
Furthermore, there are success stories of IoT SSH implementation in the healthcare sector. By using SSH, healthcare providers were able to remotely monitor and manage medical devices, such as patient monitors and diagnostic equipment. This allowed them to provide real-time updates and alerts to healthcare professionals, improving patient care and outcomes.
Overall, these case studies demonstrate the benefits and capabilities of IoT SSH implementation, showcasing how organizations and individuals have leveraged this powerful remote access method to enhance the efficiency and productivity of their IoT projects and achieve their goals.
Future Trends in Remote Access and IoT
The future of remote access and IoT is expected to be shaped by several key trends and developments, driving innovation and transformation across various sectors. One of the major trends is the increasing adoption of edge computing, which involves processing data closer to the source rather than relying on centralized cloud servers. This approach reduces latency and improves the efficiency and reliability of IoT networks, enabling faster and more responsive remote access.
Another significant trend is the growth of 5G networks, which offer higher speeds, lower latency, and increased capacity compared to previous generations of cellular networks. This will enable more seamless and reliable remote access to IoT devices, particularly in areas with limited connectivity. The increased bandwidth and capacity of 5G networks will also facilitate the deployment of more complex and data-intensive IoT applications, driving further innovation and development in the field.
Furthermore, the integration of artificial intelligence (AI) and machine learning (ML) into IoT networks is expected to enhance the capabilities and performance of remote access solutions. By leveraging AI and ML, IoT devices can become more intelligent and autonomous, enabling them to make decisions and take actions without human intervention. This will drive further automation and orchestration of IoT systems, improving efficiency and productivity.
Overall, these trends are expected to shape the future of remote access and IoT, driving innovation and transformation across various sectors and enabling new and exciting possibilities for the development and deployment of IoT solutions.
FAQs
What is the main advantage of using SSH for remote access?
SSH provides a secure and encrypted channel for communication, ensuring that data transmitted between devices remains confidential and protected from unauthorized access. This is crucial for maintaining the security and integrity of IoT networks, where sensitive data is often exchanged.
Can I use SSH on devices other than Raspberry Pi?
Yes, SSH is a widely used protocol that can be used on a variety of devices, including computers, servers, and IoT devices. It provides a secure and reliable method for remote access and management, regardless of the device or operating system.
Are there any security risks associated with SSH access?
While SSH is a secure protocol, there are potential security risks if not properly configured and managed. It's important to use strong authentication methods, regularly update software and encryption algorithms, and monitor access logs to detect any suspicious activity or unauthorized access attempts.
What are some alternative methods for remote access to IoT devices?
Alternative methods for remote access to IoT devices include Virtual Network Computing (VNC), cloud-based IoT platforms, and remote desktop protocols such as Remote Desktop Protocol (RDP) and Secure Shell File Transfer Protocol (SFTP). These methods offer different features and capabilities, providing users with a range of options for managing and accessing their IoT devices.
How can I optimize Raspberry Pi performance for IoT applications?
To optimize Raspberry Pi performance for IoT applications, choose a lightweight and optimized operating system, regularly update software and operating systems, monitor and manage CPU, memory, and storage usage, and optimize network settings to ensure a stable and reliable connection.
What are the future trends in remote access and IoT?
Future trends in remote access and IoT include the increasing adoption of edge computing, the growth of 5G networks, and the integration of artificial intelligence (AI) and machine learning (ML) into IoT networks. These trends are expected to drive innovation and transformation across various sectors, enabling new and exciting possibilities for the development and deployment of IoT solutions.
Conclusion
In conclusion, the integration of remote access solutions like SSH into IoT platforms, particularly on devices like Raspberry Pi, offers significant benefits in terms of security, efficiency, and flexibility. By simplifying the process of setting up SSH and exploring alternative remote access methods, users can enhance the management and monitoring of their IoT projects. The future of IoT and remote access is promising, with emerging trends such as edge computing, 5G networks, and AI integration set to drive further innovation and development. By staying informed and adopting best practices, users can harness the full potential of IoT and remote access to achieve their goals and drive transformation across various sectors.