Accessing your Raspberry Pi remotely is essential for managing projects, automating tasks, or troubleshooting issues. However, doing so when your device is behind a firewall can seem daunting. Fortunately, there are reliable methods to SSH to Raspberry Pi behind firewall without compromising security or performance. Whether you're a hobbyist, developer, or IT professional, understanding these techniques can save you time and effort. This guide will walk you through the steps to establish a secure connection, even in restrictive network environments.
When your Raspberry Pi is located behind a firewall, traditional SSH methods may fail due to blocked ports or restricted access. This can be frustrating, especially if you rely on your Pi for critical applications. However, with the right tools and configurations, you can bypass these limitations seamlessly. From leveraging third-party services to configuring your network, we'll explore practical solutions tailored to your needs.
Our goal is to provide a comprehensive resource that empowers you to connect to your Raspberry Pi securely and efficiently. By the end of this article, you'll have the knowledge and tools to SSH to Raspberry Pi behind firewall without any hassle. Let’s dive into the details and unlock the full potential of your Raspberry Pi.
Read also:Uncover Stana Katics Alluring Physique Height Weight And More A Comprehensive Look
Table of Contents
- What is SSH and Why is it Important?
- How to SSH to Raspberry Pi Behind Firewall Without Port Forwarding?
- Is There a Way to SSH to Raspberry Pi Without Changing Firewall Settings?
- Step-by-Step Guide to Configure SSH for Raspberry Pi Behind Firewall
- What Are the Best Tools for Remote Access to Raspberry Pi?
- How to Use Third-Party Services for SSH to Raspberry Pi?
- Common Challenges When SSHing to Raspberry Pi Behind Firewall
- Why Security Matters When Accessing Raspberry Pi Remotely?
- Tips for Optimizing SSH Performance on Raspberry Pi
- Final Thoughts on SSH to Raspberry Pi Behind Firewall Without
What is SSH and Why is it Important?
SSH, or Secure Shell, is a cryptographic network protocol used for secure communication between two devices over an unsecured network. It is widely used to access remote systems, execute commands, and transfer files securely. For Raspberry Pi users, SSH is a vital tool for managing their devices remotely, especially when physical access is not possible.
One of the main advantages of SSH is its ability to encrypt data, ensuring that sensitive information, such as login credentials, remains protected from unauthorized access. This makes it an ideal choice for accessing your Raspberry Pi behind firewall without exposing your network to potential threats.
Understanding how SSH works is crucial for anyone looking to manage their Raspberry Pi effectively. By mastering SSH, you can unlock the full potential of your device, whether you're running a home server, developing IoT applications, or experimenting with automation projects.
How to SSH to Raspberry Pi Behind Firewall Without Port Forwarding?
Port forwarding is a common method for enabling SSH access to devices behind a firewall. However, not everyone has the ability or permission to configure their router settings. The good news is that you can SSH to Raspberry Pi behind firewall without port forwarding by using alternative methods.
One popular approach is to use a reverse SSH tunnel. This involves setting up a connection from your Raspberry Pi to an external server, which acts as a bridge for incoming SSH requests. By doing so, you can bypass the need for port forwarding entirely. Here’s how it works:
- Set up an external server with a public IP address.
- Install and configure an SSH client on your Raspberry Pi.
- Create a reverse SSH tunnel from the Pi to the external server.
- Connect to the external server from your local machine to access the Pi.
This method is secure and reliable, making it an excellent choice for users who want to SSH to Raspberry Pi behind firewall without modifying their network settings.
Read also:Kash Patels Personal Life Marriage Biography And More A Comprehensive Insight
Is There a Way to SSH to Raspberry Pi Without Changing Firewall Settings?
Yes, there are ways to SSH to Raspberry Pi behind firewall without altering your firewall settings. One such method involves using a cloud-based service like ngrok or PageKite. These services create a secure tunnel between your Raspberry Pi and the internet, allowing you to access it remotely without exposing your network to risks.
To use ngrok, follow these steps:
- Download and install ngrok on your Raspberry Pi.
- Start an SSH session on your Pi.
- Run the ngrok command to create a tunnel for port 22 (the default SSH port).
- Use the provided ngrok URL to connect to your Pi from any device.
This approach is particularly useful for users who want a quick and hassle-free solution to SSH to Raspberry Pi behind firewall without making permanent changes to their network.
Step-by-Step Guide to Configure SSH for Raspberry Pi Behind Firewall
Configuring SSH for a Raspberry Pi behind a firewall requires careful planning and execution. Below is a step-by-step guide to help you set up a secure connection:
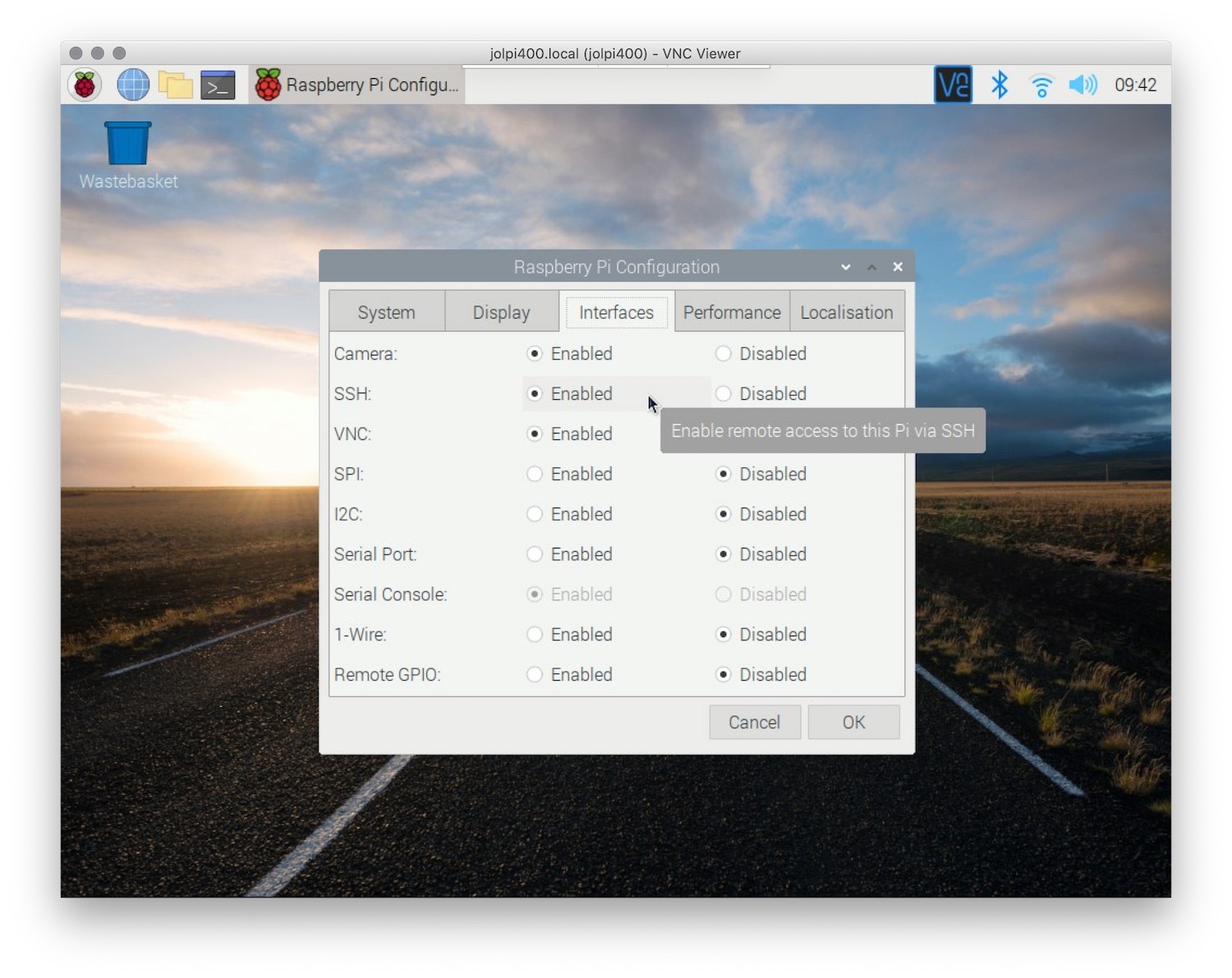
- Enable SSH on your Raspberry Pi by accessing the Raspberry Pi Configuration tool or editing the
sshfile in the boot directory. - Set a strong password for your Pi to prevent unauthorized access.
- Install and configure a dynamic DNS service to assign a domain name to your Pi’s IP address.
- Use a reverse SSH tunnel or a third-party service to bypass firewall restrictions.
- Test the connection from an external device to ensure everything is working correctly.
By following these steps, you can SSH to Raspberry Pi behind firewall without compromising security or performance.
What Are the Best Tools for Remote Access to Raspberry Pi?
Choosing the right tools can make a significant difference when accessing your Raspberry Pi remotely. Here are some of the best tools available:
- ngrok: A cloud-based service that creates secure tunnels for remote access.
- PageKite: A lightweight solution for exposing your Pi to the internet.
- ZeroTier: A virtual networking platform that allows you to create private networks for secure communication.
- Tailscale: A user-friendly tool for setting up secure connections between devices.
Each of these tools has its own strengths, so it’s important to choose one that aligns with your specific needs and technical expertise.
How to Use Third-Party Services for SSH to Raspberry Pi?
Third-party services like ngrok and ZeroTier offer simple and effective ways to SSH to Raspberry Pi behind firewall without dealing with complex configurations. These services are particularly useful for beginners or users who want a hassle-free solution.
For example, ZeroTier allows you to create a virtual private network (VPN) that connects your devices securely. Once installed, you can access your Raspberry Pi as if it were on the same local network, eliminating the need for port forwarding or firewall adjustments.
Common Challenges When SSHing to Raspberry Pi Behind Firewall
While SSH is a powerful tool, there are some challenges you may encounter when trying to SSH to Raspberry Pi behind firewall without proper preparation. These include:
- Blocked ports preventing SSH connections.
- Firewall rules that restrict incoming traffic.
- Dynamic IP addresses that change frequently.
Understanding these challenges can help you plan and implement effective solutions to overcome them.
Why Security Matters When Accessing Raspberry Pi Remotely?
Security is a top priority when accessing your Raspberry Pi remotely. Without proper safeguards, your device could become vulnerable to cyberattacks, leading to data breaches or unauthorized access.
To enhance security, consider implementing the following measures:
- Use SSH keys instead of passwords for authentication.
- Disable root login to prevent brute-force attacks.
- Keep your Raspberry Pi’s operating system and software up to date.
Tips for Optimizing SSH Performance on Raspberry Pi
Optimizing SSH performance can improve your experience when accessing your Raspberry Pi remotely. Here are some tips:
- Use compression to reduce data transfer times.
- Limit the number of open SSH sessions to conserve resources.
- Monitor your Pi’s CPU and memory usage to identify potential bottlenecks.
Final Thoughts on SSH to Raspberry Pi Behind Firewall Without
Accessing your Raspberry Pi remotely is a valuable skill that can enhance your productivity and expand the capabilities of your device. By leveraging the methods and tools discussed in this article, you can SSH to Raspberry Pi behind firewall without facing unnecessary obstacles.
Remember to prioritize security and choose solutions that align with your technical expertise. With the right approach, you can unlock the full potential of your Raspberry Pi and enjoy seamless remote access.